In today’s digital-first world, video conferencing has become the backbone of communication for businesses, educators, and healthcare providers alike. However, as virtual meetings expand, the risks of data breaches and unauthorized access also increase. This comprehensive guide to secure video conferencing explains how to safeguard your online meetings through advanced encryption, authentication methods, and compliance measures, creating a safer and more reliable communication environment in 2025.
What is Video Conferencing Security?
Video conferencing security is designed to protect video calls from unauthorized access, ensuring that digital interactions remain confidential and secure. This is increasingly important as remote work and virtual meetings become more prevalent. Key security measures include the encryption of transmitted data—covering video, audio, and shared files—to prevent unauthorized interception. Authentication protocols are also essential, verifying the identity of all participants to protect against uninvited access.
Furthermore, video conferencing security involves controlling user permissions within a call through authorization controls and securely storing any recorded sessions and transferred files. The network infrastructure itself must be safeguarded against attacks that could compromise the integrity of a video conference. A cornerstone of robust video conferencing security is end-to-end encryption, which ensures that only communicating users can decrypt and access the transmitted data, thereby maintaining the utmost privacy and compliance with regulatory standards.
Potential Risks of Video Conferencing
Video conferencing has become an essential tool for modern communication, connecting teams and clients across the globe. However, as its usage grows, so do the potential risks that can compromise privacy, data security, and user trust.
- Data Breaches – Sensitive information shared during meetings can be intercepted if encryption is weak or improperly configured.
- Unauthorized Access – Poor password management or unsecured meeting links can allow outsiders to join confidential sessions.
- Phishing and Malware Attacks – Fake meeting invitations or malicious links can trick participants into revealing credentials or downloading harmful software.
- Recording Leaks – Unprotected or automatically stored recordings may expose private discussions to unintended audiences.
- Privacy Violations – Inadequate consent or improper handling of participant data may lead to privacy and compliance issues.
- Network Vulnerabilities – Weak network security or outdated systems can make video platforms targets for cyberattacks.
- Human Error – Misconfigured settings, screen-sharing mistakes, or poor access controls can lead to unintended data exposure.
Practical Security Measures for Video Conferencing
To keep your video conferences secure, consider implementing the following measures:
- Enable End-to-End Encryption (E2EE): Turn on E2EE in your platform settings. Tools like Zoom and Microsoft Teams offer encryption to prevent data interception.
- Use Meeting Passwords and Waiting Rooms: Set a unique password for every meeting and enable the waiting room feature so the host can manually approve participants.
- Restrict Screen Sharing: Allow only the host or selected participants to share their screens to prevent unauthorized content sharing.
- Keep Software Updated: Regularly update your conferencing software, operating system, and antivirus programs to fix known vulnerabilities.
- Disable Automatic Recording: Record meetings only when necessary, and store recordings in encrypted or access-controlled folders.
- Require Secure Logins: Ask employees to use company email accounts and enable two-factor authentication (2FA) for added security.
- Lock the Meeting: Once all participants have joined, use the “lock meeting” feature to block additional attendees.
- Delete Old Links: Remove or expire outdated meeting links after each session to prevent reuse.
- Use a Secure Network: Avoid public Wi-Fi. If needed, connect through a VPN for safer communication.
- Provide Security Training: Educate employees to recognize phishing attempts and fake meeting invitations.
Best 10 Secure Video Conferencing Solutions to Consider
Here, we introduce 10 secure video conferencing software apps that stand out for their commitment to user security and data integrity, providing peace of mind in a world where online communication is ubiquitous.
1. Zoom

Zoom is a widely used video conferencing solution celebrated for its user-friendly interface. It is designed to handle large groups of up to 1,000 participants. The platform comprises features such as screen sharing, virtual backgrounds, and breakout rooms, all working together to provide an immersive meeting experience. To ensure the security of its users, Zoom has implemented multiple measures such as end-to-end encryption, two-factor authentication, and waiting rooms to prevent uninvited guests from crashing virtual meetings.
You may also like: How to Build A Video Conferencing Zoom Clone App
2. Microsoft Teams

Microsoft Teams is an all-in-one video conferencing software that integrates with Microsoft Office 365 tools, providing a seamless meeting experience. Teams employ advanced security measures like encryption, multi-factor authentication, and secure data centers. This service supports up to 250 participants and includes features like live captions, background blur, and recording.
3. Google Meet

Google Meet is a web-based video conferencing app well-liked for its integration with other Google Workspace tools. Supporting up to 250 participants, Google Meet offers features like screen sharing, live captions, and breakout rooms. It implements advanced security measures, including encryption and secure-by-default principles, to protect user data.
4. Cisco Webex

Cisco Webex is a video conferencing platform supporting up to 1000 participants. Advanced features like virtual backgrounds, screen sharing, and recording enhance virtual meetings. Cisco uses top-notch security measures like end-to-end encryption and secure data centers to safeguard user data. Webex also offers noise cancellation and real-time translation features, further elevating the virtual meeting experience.
5. BlueJeans
BlueJeans is a cloud-based video conferencing software highly regarded for its ease of use and reliable performance. It offers various useful features such as recording, screen sharing, and virtual backgrounds, allowing up to 150 participants to collaborate seamlessly. BlueJeans has implemented robust security measures, such as end-to-end encryption, to protect user data from cyber threats. The platform also complies with rigorous security standards such as ISO 27001 and SOC 2, making it an ideal choice for those prioritizing data security.
6. GoTo Meeting
GoTo Meeting is a professional online meeting solution that provides reliable and secure video conferencing features. Known for its robust performance and ease of use, GoTo Meeting offers end-to-end encryption and multiple security settings to keep meetings private. Users can host or join meetings from anywhere, share screens, and collaborate effectively with HD video and clear audio. The platform supports various integrations with popular business tools, enhancing productivity for teams of all sizes.
7. Zoho Meeting
Zoho Meeting is a secure online conferencing platform designed for businesses and individuals who need to collaborate remotely without compromising security. It emphasizes user privacy and data protection, with SSL/128-bit AES encryption protocols for all communications. Zoho Meeting facilitates webinars and meetings with features like screen sharing, recording, and cloud storage. Its straightforward interface and no-download webinar options make it accessible for users, while integration with Zoho’s suite enhances workflow continuity.
8. Adobe Connect
Adobe Connect stands out with its customizable virtual rooms and secure video conferencing capabilities. Designed for enterprises and educators, it provides a highly secure environment with compliance with various standards, including SOC 2 Type 2. Adobe Connect allows users to create immersive virtual meeting experiences with customizable layouts, multimedia support, and interactive features. It’s ideal for training, webinars, and team collaboration, offering powerful analytics and support for mobile devices to facilitate learning and decision-making on the go.
9. Jitsi Meet
Jitsi Meet is an open-source video conferencing solution that offers secure and scalable communication options without the need for accounts or software installations. It provides high-quality video and audio conferencing with encryption by default, ensuring that all communications are protected. Features like screen sharing, meeting recording, and live streaming make Jitsi Meet versatile for personal and professional use. Its open-source nature allows developers to customize and extend functionalities to fit specific needs.
10. RingCentral Video
RingCentral Video is a comprehensive solution for video meetings and team messaging that emphasizes security and ease of use. It supports end-to-end encryption, ensuring that all communications remain private. With features like screen sharing, integrated chat, and file sharing, it’s designed to boost collaboration among teams. RingCentral Video seamlessly integrates with other business applications and offers robust administrative controls, analytics, and 24/7 support, making it suitable for businesses seeking reliable and secure video conferencing options.
Best Practices for Secure Video Conferencing
To ensure secure video conferencing and safeguard sensitive information, follow these best practices:
- Use End-to-End Encryption: Opt for platforms that provide end-to-end encryption to ensure that only the intended participants can access and decrypt the communication.
- Control Meeting Access: Employ meeting passwords and waiting rooms to control access, and directly share meeting links with intended participants to avoid unauthorized entry.
- Regularly Update Software: Keep your video conferencing software up to date to protect against known vulnerabilities and ensure access to the latest security features.
- Limit Screen Sharing: Configure settings to limit screen sharing to the host or specific participants to prevent the display of unwanted or sensitive content.
How Can ZEGOCLOUD Help with Secure Video Conferencing
ZEGOCLOUD is a cloud-based platform that offers a range of UIKits and video conferencing APIs to help businesses build secure and effective virtual communication solutions. With ZEGOCLOUD, you can create a customizable, branded video conferencing platform that meets your organization’s needs.
ZEGOCLOUD UIKits provides a set of pre-designed and customizable UI elements that you can use to build a branded video conferencing platform quickly. For modularity, ZEGOCLOUD offers a dedicated UIKit for video conferencing, known as Video Conference Kit.
Some of the key features of the ZEGOCLOUD Video Conference Kit include:
1. End-to-End Encryption
ZEGOCLOUD provides end-to-end encryption, ensuring your video conferences are secure and your data is protected.
2. Multi-Party Conferencing
ZEGOCLOUD allows you to host multi-party video conferences, enabling you to connect with multiple participants from different locations simultaneously.
3. Screen Sharing
With ZEGOCLOUD, you can share your screen with other participants, making it easier to collaborate and share information during virtual meetings.
4. Recording and Playback
ZEGOCLOUD allows you to record your video conferences and play them back later, enabling you to review important information and ensure nothing is missed.
Steps to Make Secure Video Conferencing Software
Follow the steps below to build a secure video conferencing app using the ZEGOCLOUD:
- To get started with ZEGOCLOUD, sign up or log in to the admin console. This will give you access to the tools and resources you need to build your secure video conferencing system.
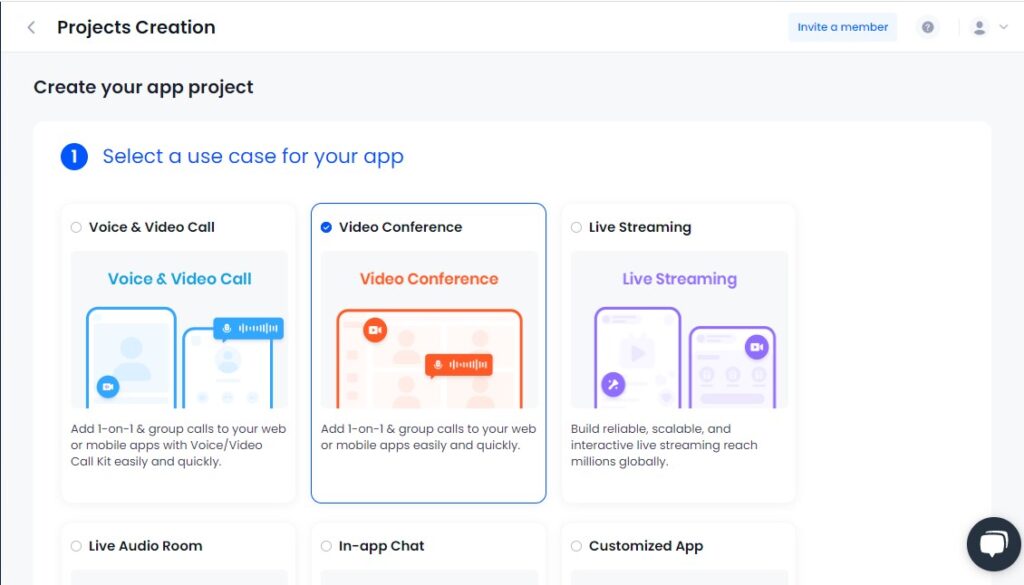
- After logging in, create a new project in the admin dashboard. This project will serve as the foundation for your video conferencing app, and you can customize it to meet your specific needs.
- Next, choose the app use cases you want to support with your video conferencing app. This could include anything from internal team meetings to client presentations.
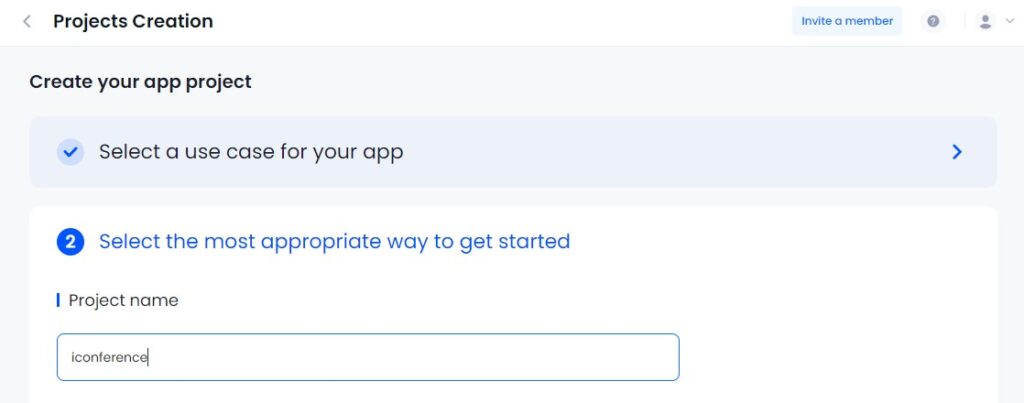
- Choose an app name of your choice. Users will see this name when they access your video conferencing app.
- Select “UIKits”, which is a user interface development framework that provides a set of pre-built user interface components that you can use to design your video conferencing app.
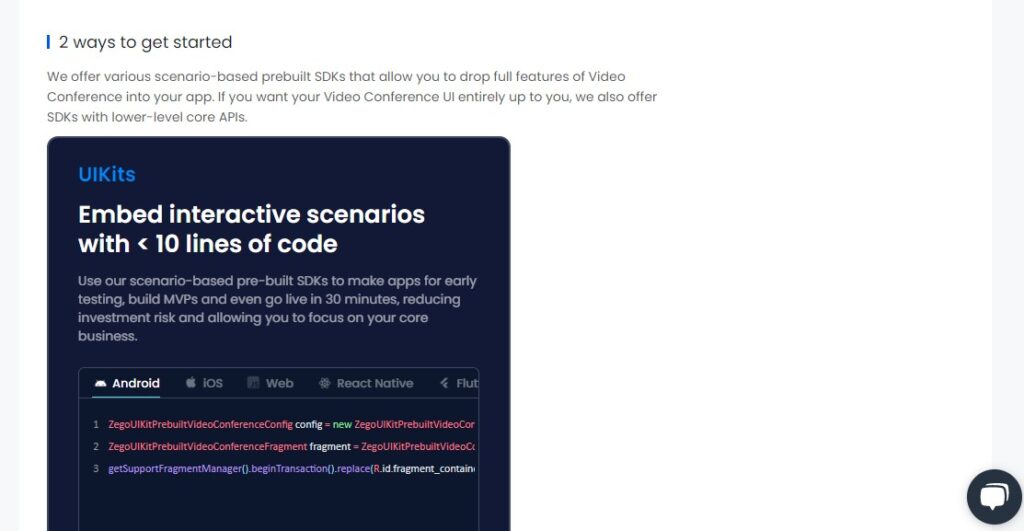
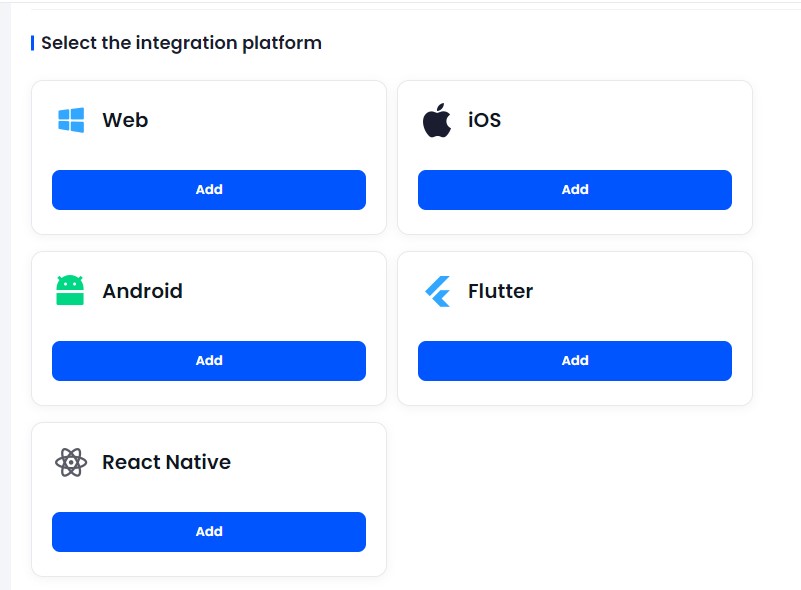
- Select the platform of your choices, such as iOS or Android, depending on where you want your app to be available.
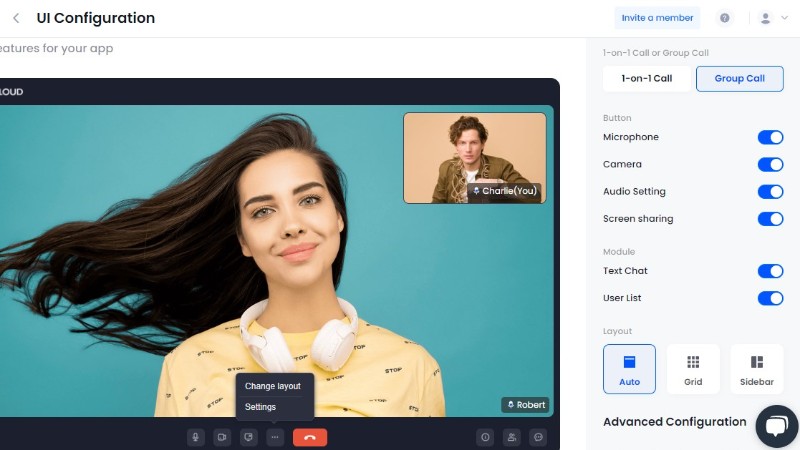
- Make UI configurations to match your specific purpose. This will allow you to customize the look and feel of your app to match your brand and meet your particular requirements.
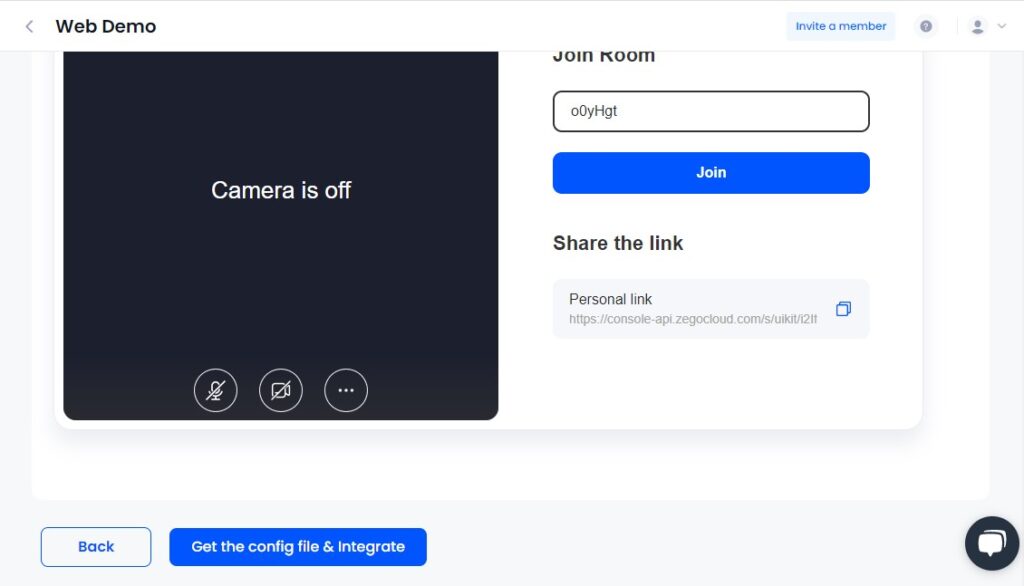
- Finally, click “Get configuration file and integrate to download project” to download your project configuration file. Make any necessary corrections to the file to ensure that your video conferencing app is configured correctly and works as expected.
Final Thoughts
The 10 video conferencing software above provides reliable and advanced features to enhance virtual meetings. Whether you need to host a small meeting or a large conference, these video conferencing software can help you achieve a seamless and secure virtual meeting experience. If you want to build a video conferencing app, ZEGOCLOUD is a top option for building secure video conferencing apps.
Read more:
- Best 5 HIPAA-Compliant Video Conferencing Platforms
- 5 Best Video Call Background Options for Video Conferencing
FAQ
Q1: What is secure video conferencing?
It refers to using encryption, authentication, and privacy controls to ensure that only authorized participants can join and that meeting data remains confidential.
Q2: Why is video conferencing security important?
Sensitive business discussions, financial data, or personal information shared in meetings can be stolen or misused if not properly protected.
Q3: How can I make my video conferences more secure?
Use end-to-end encryption, strong passwords, waiting rooms, and two-factor authentication. Keep your software updated and limit screen sharing.
Q4: What are the biggest security risks in video conferencing?
Risks include unauthorized access, data breaches, phishing attacks, unencrypted recordings, and privacy violations.
Q5: Is Zoom or Google Meet secure for business use?
Both platforms have improved security features, but users should still enable E2EE, use passwords, and control meeting access manually.
Let’s Build APP Together
Start building with real-time video, voice & chat SDK for apps today!