The need to protect online data grows every day as apps and services handle more private information. On the other hand, traditional login systems usually fall short when it comes to both safety and ease of use. That’s where token-based authentication offers a safer way for users to access digital tools without sharing passwords. Thus, this article explains what it is, how it works, and why it matters in today’s digital world.
What is Token-Based Authentication?
This authentication method is basically a way to check if a user is real without asking for a password every time. When someone logs into an app or website, the system actually gives them a minor digital key called a token. Thus, this key lets them use the service without needing to log in again for each request. At this point, the user must first enter their username and password on the platform.
In case the details are correct, the server gives them an auth token, which basically acts like a digital pass. It stays active only for a set time or until the user logs out of the service. Besides, this helps keep user data safe and limits unwanted access to private information. Hence, unlike older login methods, token-based systems give more control and better security to both users and app owners.
A History of Authentication Tokens
Before token systems existed, people used passwords to protect accounts and digital spaces. Additionally, users had to remember their passwords and type them every time they wanted access. Even early computer systems faced password theft as far back as the 1960s. As the internet grew, the authentication token became a better way to protect users.
Moreover, it allowed people to log in once and safely move through apps without entering their password again. Some modern tokens, like JWT, are a secure way to represent claims between two parties. Plus, JWTs are mostly used in modern web applications and APIs due to their flexibility and security features. Today, token-based systems continue to improve and give both users and developers more trust and control.
5 Authentication Token Types
There are several types of authentication tokens, and each serves a special purpose. Thus, let’s explore the 5 common types that are mostly used in token-based auth systems today:
1. Access Tokens
They are used in many modern systems to give users permission to use a service. Moreover, these tokens follow the OAuth 2.0 rules and carry limited details about the user or system. They don’t show identity but tell the system what the user is allowed to do. Accordingly, access tokens are a big part of token-based authentication and help apps control access without asking for login details again.
2. ID Tokens
These tokens are mostly used with OpenID Connect and come in a format called JWT. Alongside that, they carry key details like the user’s name and when the token was made. Unlike access tokens, apps can read ID tokens to check identity. Besides, this authentication token helps apps know the person using the service, which plays a key role by making sure only the right people can enter.
3. Self-Signed JWTs
In this type of token, the app or user creates a self-signed JWT without using a central server. Furthermore, this method is usually used when developers want to access services like Google APIs directly. In addition, the token includes both the identity and permissions inside it. Though this method works well, it ultimately needs careful handling to keep it safe.
4. Refresh Tokens
It allows users to stay logged in for a longer time without re-entering passwords. When an access token runs out, the app uses the refresh token to ask for a new one. In addition, this keeps the user session going. It is usually stored in apps and is not shared with others. This token-based auth improves ease of use and safety by making login smooth while still protecting data.
5. Bearer Tokens
Bearer tokens give anyone who holds them access, like a concert ticket shown at the entrance gate. Moreover, access tokens, ID tokens, and even self-signed JWTs are all part of the Auth Token Bearer family. Similarly, apps must use secure connections like HTTPS to protect bearer tokens from hackers or unwanted use. Since bearer tokens carry power, developers must care about them in security token authentication setups.
Use Cases for Token-Based Security
Many apps and systems now use token-based authentication to control access, protect data, and keep users logged in. Below, we will look at where and how different platforms use authentication token systems to make digital experiences safer:
1. Web Applications
Web apps mostly rely on it to keep users logged in without storing session data on the server. When users sign in, the server sends an auth token that the browser uses for future requests. Additionally, this method works well in systems where many users access the app from different devices or locations. As the system stays stateless, apps can grow without worrying about complex session tracking issues.
2. Mobile Applications
These apps opt for token-based auth to let users stay logged in and interact with cloud services safely. Once users sign in, the app stores a token that works each time they open or refresh the app. This way, users can enjoy quick access without having to try their credentials again and again during the day. Moreover, tokens move with requests and confirm identity without using passwords repeatedly across app actions.
3. API Security
APIs connect services and servers, and they need token-based authentication to block unwanted requests. Moreover, apps basically send a token with each API call, and the server checks if it’s valid before sharing any data. Tools like JWTs or API keys help confirm each user’s identity during every interaction with the system. Thus, this kind of security token authentication is key in any app that collects data through APIs.
4. Single Sign-On
This system also uses token-based auth to let users access many apps using one login and a shared token. After one successful login, the system sends a token that other apps can use to confirm the same user. Therefore, it saves time and reduces password fatigue because users don’t need to sign in to each app again. With proper setup, SSO can improve user experience while keeping security rules in place.
5. Internet of Things
IoT devices use authentication token systems to talk with cloud services or each other without human help. Additionally, tokens allow each smart device to send or receive data only if it confirms its identity with the central server. Similarly, this makes communication faster, safer, and less likely to be blocked or hacked by outsiders. Security token authentication supports millions of devices running at once, often in real-time environments.
How Does the Token-Based Authentication Work?
Every time users log in to an app or site, security token authentication keeps their data safe and their session smooth. Thus, let’s dive below to discover the key steps behind how this system works in real-time across platforms:
1. User Login Request
The process starts when the user enters their login details in the app or website’s display. These details can include a username, password, fingerprint, or other form of identity check. Once the user submits the login form, the app collects this data and prepares it for checking. Then, this step begins the process of creating a unique and secure-auth token.
2. Verification by Server
In addition, the app sends the login data to the server to confirm if the user exists and the details match. When everything looks correct, the server creates an authentication token in a special secure format. Besides that, the token usually includes three main parts: the header, payload, and signature.
3. Token Use and Validation
Upon doing verification, the user now gets the token and sends it each time they request access to app data or a feature. Similarly, the system checks if the token is real and still valid before allowing anything to be shown or used. Alongside that, these tokens usually expire quickly, so no one else can reuse them in case of a breach.
4. Token Storage During the Session
Whenever the token is checked and access is approved, the system stores it for the session time. At this time, the session entirely depends on the type of app and the security level required by the app. Moreover, the server keeps the auth token only while the user stays active on the site. Once they log out or remain idle for too long, the token becomes useless for safety reasons.
Authentication Token Best Practices
To make the most of token-based security, you need to follow smart steps that protect both users and systems every time. Therefore, below are the best practices that keep every token-based authentication safe during login and session activities across all apps:
- Keep Tokens Private: Each user should use their own token without sharing it with anyone else at any point in time. In addition, each authentication token should be treated like a password and never allow users to pass it between people or teams.
- Use Secure Connections: Always make sure the app or website uses HTTPS when sending any data, including authentication token details. Moreover, encryption blocks others from reading or stealing token data while it moves securely between your app and the server.
- Test Your Tokens Regularly: It is also recommended that you run regular checks on your tokens to confirm that everything works in the process. Hence, testing helps you spot weak spots early and fix them before they become a bigger problem.
- Opt for the Right Token Type: Not every authentication token fits every task or app need, so always choose the correct token for each case. Some tokens work well for short sessions, while others offer strong safety features needed for more advanced systems.
How ZEGOCLOUD Enhances Token-Based Authentication in Real-Time Applications
ZEGOCLOUD basically secures user identity and access by generating tokens on your server using your AppID and ServerSecret only. Additionally, it provides a free Token Generator plug-in on GitHub, which supports Java, Python, and .NET. Hence, you can use the Kit Token to control who enters which room and define each user’s unique ID. It also uses token-based authentication to protect every login and user permission inside your instant application.
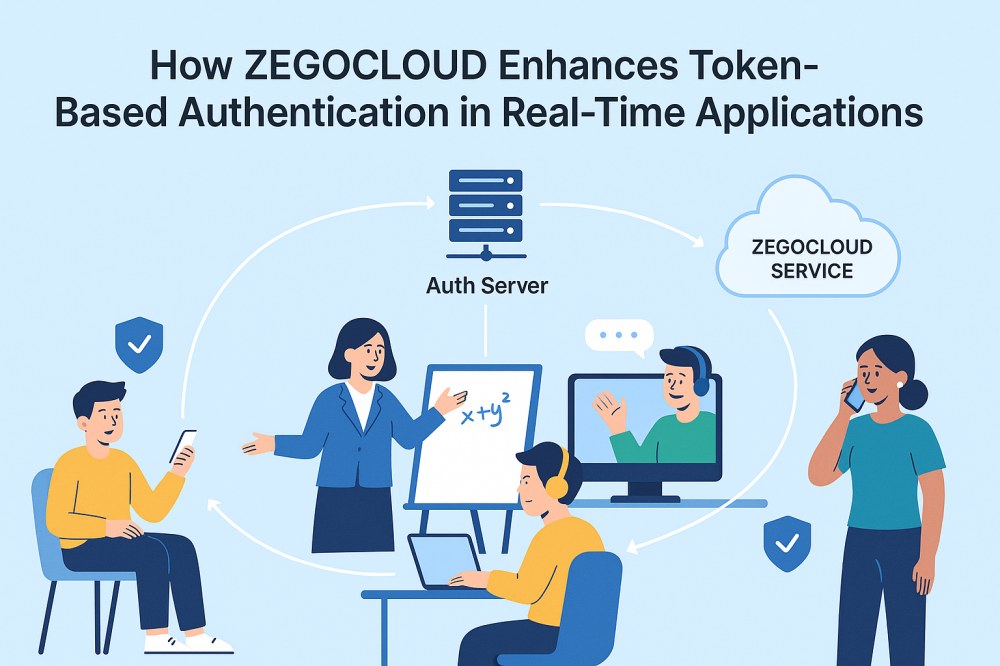
When a user’s authentication token expires, the SDK doesn’t kick them out but blocks future logins or streaming actions. You must upgrade to control access and secure sessions to utilize it further. Moreover, you can refresh the token early using the built-in renewToken method, which avoids user disruption during active sessions. Besides, ZEGOCLOUD provides different modes, such as AppSign, Token-preferred, and Token-only, with each offering various levels of security control.
The Token-only mode ensures security token authentication by blocking fallback to AppSign, making token use the only valid method. After SDK version 2.17.0, ZEGOCLOUD forces the use of auth tokens to continue using real-time voice or video services. Moreover, it disables AppSign from the Admin Console, so users must use tokens to maintain access and session safety.
Conclusion
To conclude, token-based authentication gives users a safer and easier way to log in without sharing their passwords repeatedly. Moreover, it works well in apps, APIs, and smart devices by keeping sessions smooth and private.
Thus, opting for the right authentication token technique helps protect data and control access at all times. For real-time apps that need strong security and smooth login, we suggest using ZEGOCLOUD as your trusted solution.
FAQ
Q1: What is meant by token-based authentication?
Token-based authentication is a security mechanism that allows users to verify their identity using a digitally signed token instead of a username and password for every request. Once a user logs in, a token is issued by the server and included in subsequent API calls to authenticate the user in a stateless and scalable way.
Q2: What is the difference between token-based authentication and OAuth?
Token-based authentication is a general concept where a token (like a JWT) is used to verify the user’s identity. OAuth (Open Authorization), on the other hand, is an authorization framework that allows third-party apps to access user resources without sharing passwords. OAuth issues access tokens, so you can think of OAuth as a specific protocol that uses token-based authentication under the hood.
Q3: What is the difference between JWT and token-based authentication?
JWT (JSON Web Token) is a specific format for tokens used in token-based authentication. Token-based authentication is the broader concept, while JWT is one way to implement it. JWTs are self-contained, meaning they store user data and permissions directly inside the token, which allows for stateless server-side validation.
Q4: What is the difference between OTP and token?
OTP (One-Time Password) is a temporary, single-use code sent to users to verify identity — commonly used in 2FA (two-factor authentication). A token, in token-based authentication, is a reusable digital credential (e.g., JWT or OAuth token) used to authenticate a session. OTPs are short-lived and used for login verification, while tokens are used to authorize access over time.
Let’s Build APP Together
Start building with real-time video, voice & chat SDK for apps today!